About EZproxy
The problem
As information seekers have become increasingly accustomed to searching for and finding the information they need online in digital formats, libraries have shifted large portions of their budget toward licensing content from digital databases. While these licenses often provide patrons with the ability to search these databases within the library walls, they do not guarantee that patrons will be able to access that same information from other locations. The two images below show the steps of information discovery, request, and retrieval both in and out of the library when a user is attempting to access licensed content from a third party provider.
In the library
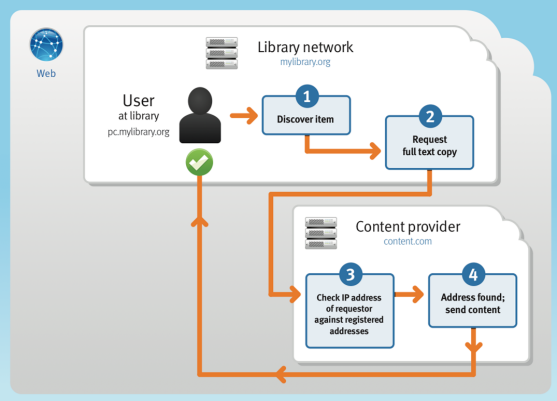
From within the library, users have easy, ready access to the databases to which your institution subscribes. From your library's homepage, a user can search and discover items they need and request a full text copy. That information will be sent directly to the content provider. At this point, your library's IP address will be checked against registered IP addresses that are allowed to access content, and once the match has been made, the content will be sent back to the user at the library.
Outside of the library
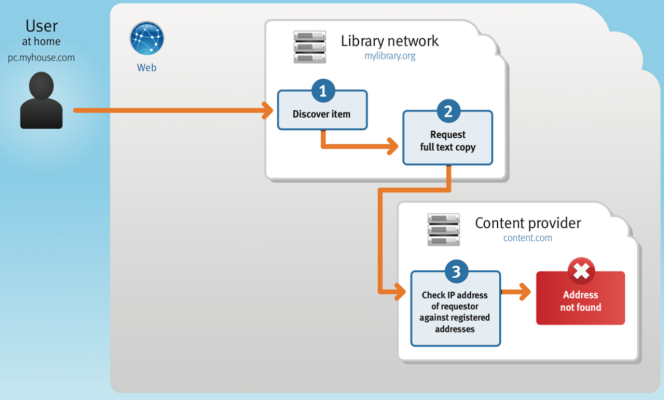
Outside of the library, user access to your institution's databases is not guaranteed. A user can still access your library's network to search and discover the needed item. They can still place a request for that item. However, when that request reaches the content provider for authentication, the user's IP address is not the same as the library's since the search did not originate from a computer in the library, on the library's network. When the content provider fails to match the user's IP address with a registered IP address, the process stops, and the user receives an error message stating access to the content is denied.
If libraries can provide access to these databases to users when and where they need it, then libraries can extend their services beyond the hours the libraries are open, save their users travel time, and provide new services to users who may need access from across town or around the world.
Unfortunately, making licensed databases available to remote users can require a great deal of work. You need to be able to authenticate that a remote user is actually one of your authorized users, then provide some mechanism for these validated users to gain access to your licensed resources. EZproxy can address both of these needs.
The solution
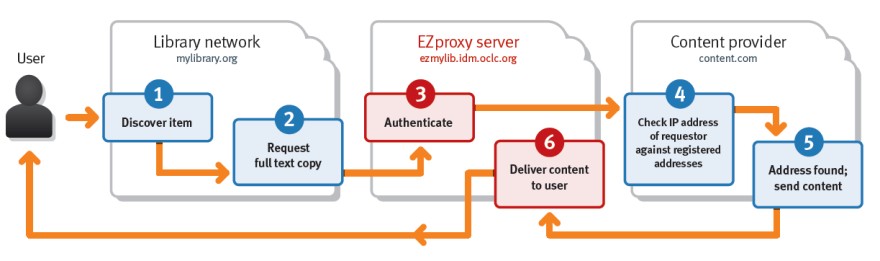
EZproxy works as an intermediary between your users and the databases they are trying to access. It confirms that your users are authorized to access your database subscriptions and delivers the e-content to them. When a user searches your institution's resources and finds e-content they would like to access, EZproxy authenticates their identity, then passes their request on to the content provider with EZproxy's IP address attached instead of the user's. The content provider then finds the EZproxy IP address as a match in its list of registered IP addresses for your institution, and passes the content back to your EZproxy server (the place where the content provider believes the request originated). EZproxy then delivers the content to the user.
OCLC offers libraries two ways to use EZproxy to make their database subscriptions available to remote users. For more information about these options, please see EZproxy Features.